Trezor.io/Start and Trezor Login – A Complete User Guide
In the world of digital assets, protecting your funds is as important as the investments themselves. With cryptocurrency becoming mainstream, security concerns have grown significantly, and hardware wallets like Trezor provide a reliable solution. The journey for every new Trezor.io/start user begins at Trezor.io/Start, the official gateway for device setup. Alongside this, learning how to properly use the Trezor login process ensures that your cryptocurrencies remain safe from online threats. Understanding both elements gives you confidence to manage your assets securely.
Introduction to Trezor Hardware Wallets
Trezor, developed by SatoshiLabs, was the first commercially available hardware wallet and has since earned its reputation as one of the most trusted tools for cryptocurrency storage. Unlike exchanges or software wallets, Trezor keeps private keys offline, ensuring they are never exposed to the internet. This means that even if your computer is infected with malware or your exchange account is compromised, your crypto remains protected. Trezor.io/Start provides a safe, step-by-step guide to initialize the device for the first time, while the Trezor login feature through Trezor Suite or the official application ensures secure access when managing assets.
Beginning at Trezor.io/Start
Every Trezor.io/start device, whether the entry-level Trezor Model One or the advanced Trezor Model T, must first be set up through Trezor.io/Start. This page ensures that you are guided to the official resources, reducing the risk of falling into phishing traps. Once you connect your device to a computer via USB, the site directs you to install Trezor Suite, the desktop application designed for wallet management. The installation process is straightforward and provides access to all features needed to interact with your digital assets.
An important part of the setup involves firmware installation or updates. New devices often require the latest firmware before creating a wallet. Firmware updates are not just cosmetic improvements; they contain vital security enhancements. Completing this step ensures that your wallet operates with the highest level of protection available at that time.
Creating and Securing the Recovery Seed
One of the most important steps during the initial setup is generating the recovery seed. The Trezor device displays a unique set of random words on its screen, which serve as the ultimate backup for your wallet. Writing these words down carefully and storing them in a secure offline location is essential. The recovery seed allows you to restore your wallet in case the device is lost or damaged. Trezor emphasizes that this seed should never be stored on a phone, computer, or any cloud service because digital storage introduces unnecessary risks.
By completing this step at Trezor.io/Start, you essentially hold the master key to your assets. The seed must be protected with the same seriousness as one would protect the PIN to a bank vault. Many users go a step further and store the words on durable, fireproof, or waterproof backup materials to protect against natural disasters.
Understanding the Trezor Login Process
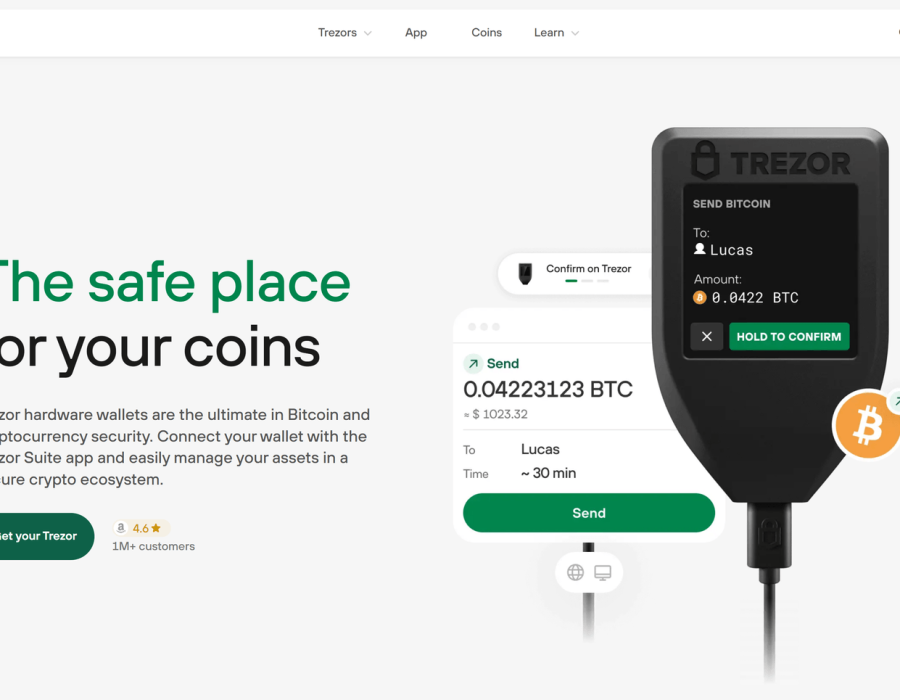
Once setup is complete, accessing your wallet is done through the Trezor login process. This occurs whenever you open Trezor Suite or use the device to connect with compatible applications. To log in, you first connect your hardware wallet to your computer. You will then be asked to enter your PIN, which is created during setup. This PIN protects the device from unauthorized use in case it falls into the wrong hands.
The login process also allows for an additional layer of protection with the optional passphrase feature. A passphrase acts like an extra password that extends the recovery seed with another word of your choice. Even if someone were to gain access to your seed, without the passphrase they cannot reach your funds. This makes the Trezor login procedure one of the most secure methods of accessing a cryptocurrency wallet.
Managing Assets After Login
After logging in, the Trezor Login interface provides access to portfolio balances, transaction history, and tools for sending and receiving crypto. Each transaction requires confirmation on the Trezor device itself, which means the details must be verified physically on the device screen before approval. This prevents attackers from secretly altering transactions on your computer. The login is therefore not just an entry step, but an integral part of protecting the flow of assets.
Trezor Suite supports multiple cryptocurrencies, giving users the ability to manage a diverse portfolio from one secure location. Updates and improvements are regularly released, and logging in ensures users benefit from the most recent security features and usability upgrades.
Common Issues and Best Practices
Some users may face challenges during login, such as forgetting the PIN or misplacing the recovery seed. Trezor provides a recovery process, but it requires the original recovery seed to restore the wallet. If both the device and the recovery seed are lost, access to funds is permanently gone, highlighting the importance of careful backup.
Best practices for login and general usage include keeping your firmware up to date, using the desktop version of Trezor Suite instead of browser extensions when possible, and always verifying transaction details directly on the device screen. Avoid logging in from public or insecure computers and make sure your personal devices are free of malware. Following these practices ensures that the strength of the Trezor system is not weakened by simple mistakes.
Final Thoughts
Trezor.io/Start and the Trezor login process form the backbone of safe cryptocurrency management for Trezor users. The setup page ensures a secure beginning with proper firmware, recovery seed creation, and software installation, while the login mechanism safeguards ongoing access. Together, they provide a balance of convenience and security in a digital world where threats are constant.




Comments