Authentication involves the process of verifying the user's identity. Security concerns mandate the requirement of authentication. With the rapid growth in technology, our perceptions of what constitutes strong security may change.
What was considered safe at the turn of the century is no longer the most suitable option in 2023. Because the internet has evolved, security procedures must evolve as well.
Below is a list of authentication methods considered as the most secure in the 21st century. Read on for more information.
1. Biometric Authentication
Biometric authentication is a data protection method that depends on a user's unique biological features. This technology is used by consumers, government entities, and private enterprises such as airports or military bases. The technology is becoming more popular due to its ability to achieve high safety while minimizing user friction.
Methods of authenticating users through biometrics include; Fingerprint scanners, Facial recognition, Eye scanners, and Speaker recognition.
Some advantages of this technology are such as;
- Controlling physical access to the property when installed in gates or doors
- Easy comparison of biological features to authorized features saved in databases
- Involvement of biometrics in multi-factor authentication processes
- Easy usage as it does not require memorizing pins or passwords
- Hard to hack due to the unique nature of individual fingerprints and retina characteristics
Despite the efficiency of biometric authentication, the technology has some disadvantages. Examples are;
- Errors, including false acceptance or false rejection of a user's authentication attempt.
- Privacy concerns from users as they worry about where biometric information is stored and whether it can be accessed or not.
2. Behavioral Authentication
Behavioral authentication is a system that employs the behavioral traits of an individual to verify their identity. This is achieved by assessing their behavioral patterns in real-time and comparing them to consumer data saved in the device.
Everything, from the angular positions the user holds their device to the pressure exerted while typing is considered a behavioral pattern.
By assessing behavioral patterns in real-time, authentication is made more secure because it differentiates between authorized customers and cybercriminals by recognizing users based on their online behavior and interactions.
The advantages of this authentication method include the following;
- Preservation of privacy as user identity is not revealed
- Clearing any uncertainty about a user's identity by use of unique data points to continuously authenticate a user
- Impossible to hack or replicate
However, a change in the user's physical state or emotional behavior can affect this authentication method.
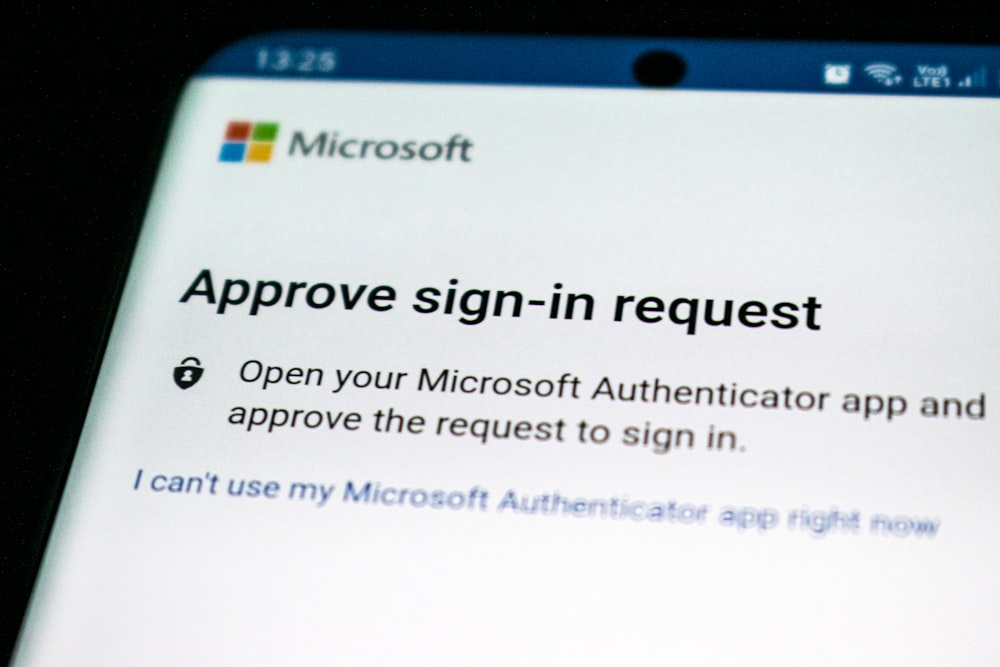
3. Push Notification Authentication
Push Notification system sends an alert to a user's device's app informing them of a login attempt. The user can investigate the details of the login attempt and, depending on their understanding of the authentication request, can either affirm or reject it.
Push notification authentication is gaining traction because it provides a simple way to authenticate users, particularly when used without passwords.
This technology has several benefits. Below are some examples.
- Users do not need to enter personal information; hence, they are more inclined to sign up.
- The duration and recurrence of notifications can be changed.
- The transition from clicking the notification to being forwarded to a particular page is smooth.
Alerts appear even when the site is closed.
Disadvantages of this technology include;
- People blocking push notifications automatically
- Push notifications are used once
- Some users assume push notifications are invasive
4. Two-Factor Authentication (2FA)
This technology involves an additional layer of security used to ensure that people attempting to access an account online are who they claim to be. For the first factor, the user will input their username and password. Instead of gaining immediate access, a second factor will be requested.
This second factor can be drawn from the following groups:
- Something you're aware of: A personal identification number (PIN), a passcode, answers to "personal questions," or a specific keyboard shortcut could all be used.
- Something you own: A user usually has something in their possession, such as a smart device or a credit card.
- Something you are: This category is somewhat more advanced, and it may include a fingerprint-based pattern, retinal scans, or a voice print.
A major advantage of 2FA is that compromising only one of the above variables will not unlock the account. Even if your passcode is hacked or your phone is misplaced, the chances of someone obtaining your second-factor information are extremely rare.
However, some downsides to the technology include;
- Prolonged login time - When logging into an application, users must undergo an additional step, which adds time to the procedure.
- Maintenance - In the absence of a reliable method for managing a user database and a variety of authentication methods, constant maintenance of this technology may prove to be a challenge
5. Multi-Factor Authentication
For authentication using this method, a user must provide two or more pieces of evidence. Adding additional authentication factors to boost security is one of MFA's main objectives.
Multi-factor verification requires at least two factors, whereas 2FA requires only two for user authentication. This means that not all MFA is 2FA, but all 2FA is MFA.
Advantages of multi-factor authentication include:
- Lowered threat to security - By using several authentication methods, the chance of human mistakes, lost devices, and forgotten passwords is not a threat to users.
- Making digital ventures possible - Companies can confidently launch digital projects. To conduct secure online engagements and transactions, businesses utilize multi-factor verification to help protect institutional and user data.
Bottom line
Authentication technology is constantly evolving. Businesses must look well outside passwords and consider authentication to improve user experience. There are several authentication methods, but the information provided above provides a summary of the most secure processes, and as a result of these improved technologies, attackers will be unable to manipulate passwords, and a data breach will be avoided.







Comments