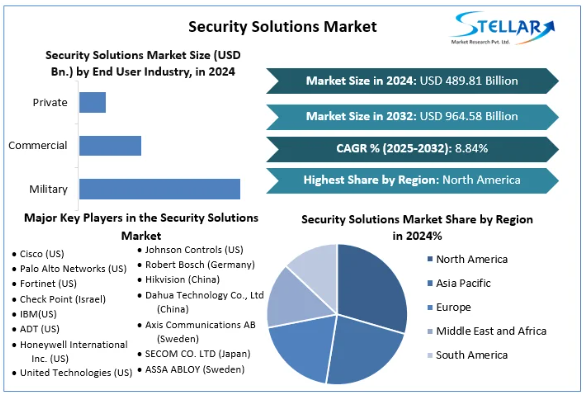
Security Solutions Market was evaluated at a size of USD 489.81 Billion in 2024 and expected to reach USD 964.58 Billion by 2032 at a CAGR of 8.84% during the forecast period.
Market Estimation & Definition
Definition & Scope
The security solutions market comprises hardware, software, and services aimed at preventing unauthorized intrusion, monitoring assets, providing access control, detecting threats (physical or digital), and safeguarding infrastructure. It spans solutions such as surveillance systems (CCTV, thermal cameras), access control, intrusion alarms, system integration, risk assessment, managed services, and maintenance.
The market is bifurcated by type into Products and Services. On the services side, key categories include system integration & consulting, risk assessment & analysis, managed security services, and maintenance & support. End-user segments include military/defense, commercial, and private/residential sectors.
This nearly doubling of market value underscores robust demand across global sectors as security becomes an integral, continuous investment rather than a one-time deployment.
Request your sample copy of this report now! https://www.stellarmr.com/report/req_sample/Security-Solutions-Market/2538
Market Growth Drivers & Opportunity
Key Drivers
- Escalating Security Threats (Physical + Cyber)
- In a world of rising terrorism, burglary, cyberattacks, insider threats, and hybrid warfare, both public institutions and private organizations are amplifying their security investments.
- Digital Transformation & IoT Proliferation
- The spread of Internet of Things (IoT) devices, connected infrastructure, edge computing, and smart cities creates new attack surfaces. Organizations require comprehensive security solutions that integrate physical and cyber protections.
- Declining Cost & Miniaturization of Hardware
- As the cost of sensors, cameras, connectivity modules, and communication modules falls, deployment becomes more accessible across geographies and scales, enabling broader adoption including in mid-size enterprises and residential markets.
- Regulatory & Compliance Imperatives
- Stricter regulatory regimes—data protection laws, critical infrastructure safeguards, building codes, surveillance mandates—are compelling organizations to adopt certified security solutions.
- Managed & Outsourced Models
- Many organizations prefer outsourcing their security to managed service providers rather than building internal capabilities. Managed security services and remote monitoring become attractive approaches, reducing capital burden.
Opportunities & Challenges
- Opportunity: Convergence of Physical + Cyber Security
- Cross-domain solutions that unify video analytics, access logs, network monitoring, anomaly detection, and AI-based threat scoring are strategic differentiators.
- Opportunity: Emerging Markets & Infrastructure Buildout
- Many developing economies are investing in surveillance, smart city frameworks, border security, and transit security systems—opening large untapped markets.
- Opportunity: AI, Analytics & Automation
- Deployment of AI for facial recognition, behavior analytics, predictive maintenance, and autonomous threat response will provide premium value and recurring service revenue.
- Challenge: Privacy & Ethical Concerns
- Mass surveillance, biometric deployment, data retention laws, and citizen consent concerns pose legal and public relations risks.
- Challenge: Integration Complexity & Legacy Systems
- Many organizations already have fragmented or legacy systems; integrating new solutions poses technical, compatibility, and cost challenges.
- Challenge: Cyberwarfare & Sophisticated Threat Actors
- Adversaries evolve rapidly; security providers must continually update capabilities, patch vulnerabilities, and respond to zero-day exploits.
Segmentation Analysis (From Report)
The report provides segmentation across type, services, and end-user industry. Below is a breakdown:
By Type
- Products
- These include hardware and software components (e.g., cameras, sensors, intrusion devices, control systems).
- Services
- Encompass system integration & consulting, risk assessment & analysis, managed security services, and maintenance & support.
The services segment is increasingly important, as annual recurring service contracts offer revenue stability and deeper customer lock-in.
By Service Type
- System Integration & Consulting
- Designing security architecture, solutions planning, deployment consulting.
- Risk Assessment & Analysis
- Threat modeling, vulnerability assessment, penetration testing.
- Managed Security Services
- Outsourced monitoring, incident response, SOC (security operations center) services.
- Maintenance & Support
- Upkeep, patching, upgrades, service contracts.
By End-User Industry
- Military / Defense
- High-end, sovereign security, border protection, critical infrastructure.
- Commercial
- Offices, retail, hospitality, corporate campuses.
- Private / Residential
- Homes, gated communities, small offices, personal use security systems.
This segmentation reflects how security deployment models differ in scale, sophistication, and budget depending on user type.
Country-Level Analysis: USA & Germany
Although the report’s summary does not fully break down each country, we can infer from its regional structure (e.g. North America, Europe) and context who the leaders are.
United States (USA)
- Dominance in North America: The North America region is typically the largest investor in security infrastructure and is a major driver of market innovation.
- In the U.S., adoption of advanced surveillance systems, access controls, biometrics, perimeter defenses, and integrated managed security services is widespread in private and public sectors.
- The U.S. defense and homeland security budgets support large contracts in surveillance, border monitoring, and cybersecurity.
- Many U.S. enterprises outsource their security operations to managed security service providers (MSSPs), SOCs, and integrators.
- The U.S. standard setting (e.g. NIST, DHS, etc.) often leads globally; vendors that succeed there gain global prestige and validation.
Germany
- Part of European Market Leadership: Germany, as one of Europe’s industrial and economic hubs, is key in European security spending.
- German enterprises and public sectors emphasize robust security for critical infrastructure, industrial plants, public transportation, and smart city deployments.
- German regulation (data privacy, GDPR compliance, privacy by design) influences how surveillance and security systems are deployed—favoring solutions that emphasize encryption, data minimization, and compliance.
- Germany’s advanced manufacturing base often demands integrated physical/cybersecurity in industrial control systems (ICS) and Industry 4.0 environments.
- The German market is likely highly competitive, with both domestic and international security firms competing on accuracy, reliability, data protection, and integration with existing industrial systems.
While numeric country values are not available in the summary, the report’s structure indicates that U.S. and German markets are treated as key national cases under North America and Europe geographies.
For additional insights into this study, please refer to:https://www.stellarmr.com/report/Security-Solutions-Market/2538
Competitive / Commutator Analysis
By “commutator analysis,” I interpret this as analyzing the competitive landscape / key players / competitive dynamics.
Major Players & Market Structure
The security solutions market is competitive and includes firms across hardware, software, and services. Though the summary does not list all names, typical players in global security space may include (but are not limited to):
- Large systems integrators
- Specialty vendors focusing on surveillance, access control, or cybersecurity
- Managed service providers
- Emerging niche firms with AI/analytics, biometrics, or IoT-based security solutions
Given the high barrier to scale (R&D, integration, reputation, service infrastructure), the market favors companies with established brand, global presence, and full-stack capabilities.
Competitive Strategies & Differentiation
- Product & Technological Innovation
- Companies compete by bringing next-gen capabilities—edge AI, sensor fusion, anomaly detection, predictive threat modeling—to market.
- Service & Managed Models
- Providers expand managed security offerings to capture recurring revenue and deeper customer relationships.
- Integration & Ecosystem Partnerships
- Forming alliances with cloud, IoT, analytics, and telecom providers helps vendors deliver complete solutions.
- Geographic Reach & Local Presence
- Local offices, data sovereignty compliance, and local partnerships improve competitiveness in diverse markets.
- Brand & Trust / Certifications
- Security is a trust business. Certifications, track record of incident handling, and compliance (ISO, regional standards) differentiate players.
Competitive Forces & Barriers
- Rivalry among existing firms: High. Many vendors compete across overlapping segments, pushing innovation and price pressures.
- Threat of new entrants: Moderate — entry is possible for niche providers with strong tech, but scale and trust take time.
- Supplier power: Moderate — suppliers of niche components (special sensors, ASICs, specialized software modules) may command leverage, but many hardware elements are commoditized.
- Buyer power: High in large contracts. Enterprises and governments negotiate contracts extensively.
- Threat of substitution: Moderate — alternative approaches (e.g. drones, satellite surveillance, swarms, or purely software cybersecurity) may act as partial substitutes or complementary threat detection approaches.
In sum, the competitive landscape requires balance of technological edge, service capability, trusted reputation, scale, and adaptability across markets.
Uncover Trending Topics :
Australia Esports Market https://www.stellarmr.com/report/Australia-Esports-Market/1586
Cash Logistics Market https://www.stellarmr.com/report/Cash-Logistics-Market/1797
Press Release Conclusion & Outlook
The Global Security Solutions Market is entering a period of dynamic growth and transformation. From USD 489.81 billion in 2024 to USD 964.58 billion in 2032, the nearly doubling valuation reflects how security—both physical and digital—is becoming foundational to infrastructure, enterprise, and daily life.
Key takeaways and future directions include:
- Convergence of physical and cybersecurity will be a hallmark of robust solutions.
- AI, analytics, automation, and edge processing will lead premium segments.
- Managed services and recurring revenue models will be critical for vendor sustainability and customer retention.
- Emerging markets and infrastructure investments present major growth opportunity, while mature markets demand sophisticated, compliant systems.
- Regulation, privacy, and ethics will be key constraints; vendors must navigate data protection and citizen rights carefully.
- Competitive advantage will accrue to those who combine technological depth, integration capability, brand trust, and global/local presence.
For stakeholders—vendors, investors, governments, integrators—the coming decade will test agility, innovation, and resilience.
About Stellar Market Research:
Stellar Market Research is a multifaceted market research and consulting company with professionals from several industries. Some of the industries we cover include science and engineering, electronic components, industrial equipment, technology, and communication, cars, and automobiles, chemical products and substances, general merchandise, beverages, personal care, and automated systems. To mention a few, we provide market-verified industry estimations, technical trend analysis, crucial market research, strategic advice, competition analysis, production and demand analysis, and client impact studies.
Contact Stellar Market Research:
S.no.8, h.no. 4-8 Pl.7/4, Kothrud,
Pinnac Memories Fl. No. 3, Kothrud, Pune,
Pune, Maharashtra, 411029
+91 20 6630 3320, +91 9607365656




Comments