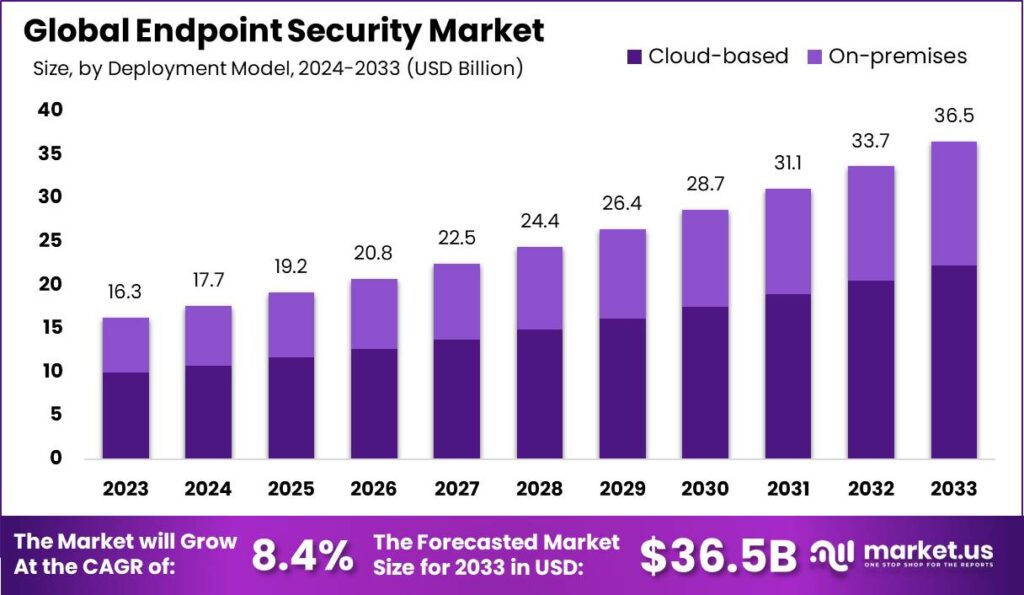
The Endpoint Security Market focuses on protecting devices such as computers, smartphones, and tablets from cyber threats. These devices, known as endpoints, are vulnerable to malware, phishing attacks, and unauthorized access, making robust endpoint security essential for safeguarding sensitive data and ensuring the integrity of corporate networks.The Endpoint Security Market is projected to reach approximately USD 36.5 billion by 2033, with a steady Compound Annual Growth Rate (CAGR) of 8.4%. In 2023, it was estimated to be worth USD 16.3 billion.In 2023, the Antivirus/Antimalware segment dominated the market with a market share of over 32%.
Growth Factors:
Several factors contribute to the growth of the endpoint security market. One of the primary growth factors is the rise in cyber attacks targeting endpoints, fueled by the value of data stored on these devices. Businesses and individuals alike are increasingly aware of the risks and are investing in endpoint security solutions to protect their sensitive information. Moreover, regulatory requirements and compliance standards mandate organizations to implement robust endpoint security measures to avoid legal consequences and safeguard their reputation.
Read more @https://market.us/report/endpoint-security-market/
Recent Trends
Emerging trends in the Endpoint Security Market include the integration of artificial intelligence (AI) and machine learning (ML) for proactive threat detection and response. AI-powered endpoint security solutions analyze endpoint behavior patterns to detect anomalies and potential threats in real-time, enhancing incident response capabilities. Furthermore, the adoption of Endpoint Detection and Response (EDR) solutions enables continuous monitoring and automated response to security incidents, improving threat visibility and mitigation.
Top Use Cases
Key use cases for Endpoint Security solutions include malware protection, encryption of sensitive data, endpoint detection and response (EDR), and application control. These solutions help organizations prevent data breaches, unauthorized access, and ensure compliance with regulatory requirements. Endpoint Security is crucial for protecting intellectual property, customer information, and maintaining business continuity in the face of evolving cyber threats.
Applications
- IT & telecom
- BFSI
- Industrial
- Retail
- Healthcare
- Government & Defense
- Education
Challenges
- Challenges in the Endpoint Security Market include the complexity of managing security across diverse endpoint devices and platforms, ensuring seamless integration with existing IT infrastructure, and addressing the shortage of skilled cybersecurity professionals.
- Budget constraints may also limit organizations' ability to invest in comprehensive endpoint security solutions.
- Additionally, balancing security with user productivity and educating end-users about cybersecurity best practices remain ongoing challenges.
Opportunities
- Opportunities in the Endpoint Security Market include advancements in AI and ML technologies, which enable predictive analytics and proactive threat mitigation.
- Cloud-based endpoint security solutions offer scalability, flexibility, and centralized management capabilities, catering to the growing adoption of cloud computing and remote work trends.
- Moreover, regulatory compliance requirements present opportunities for organizations to enhance their security posture and build trust with customers by demonstrating adherence to data protection laws.
Conclusion
In conclusion, the Endpoint Security Market plays a critical role in protecting organizations' endpoints from cyber threats in an increasingly digital and interconnected world. While facing challenges such as complexity in management, evolving threats, and skills shortages, the market presents numerous opportunities for innovation and improvement. Ensuring robust endpoint security is essential not only for protecting sensitive data but also for maintaining the trust and confidence of stakeholders in an organization's ability to safeguard against cyber threats.





Comments