At its core, cyber security encompasses a multifaceted approach aimed at safeguarding digital systems, networks, and data from unauthorized access, malicious exploitation, and disruption. It encompasses a broad spectrum of strategies, ranging from basic password hygiene to advanced threat detection algorithms. With cyber threats evolving in complexity and frequency, the need for a comprehensive cyber security framework has never been more pressing.
One of the cornerstones of effective cyber security is awareness. Users must be educated about the risks associated with their digital activities and equipped with the knowledge to identify potential threats. Phishing scams, for instance, rely on human error to gain access to sensitive information. By fostering a culture of vigilance and providing training on spotting suspicious emails or links, organizations can significantly mitigate the risk of falling victim to such attacks.
Furthermore, robust authentication mechanisms play a pivotal role in fortifying cyber defenses. Strong, unique passwords and multi-factor authentication add layers of security, making it exponentially harder for adversaries to compromise accounts. Additionally, encryption technologies ensure that data remains secure both in transit and at rest, shielding it from prying eyes.
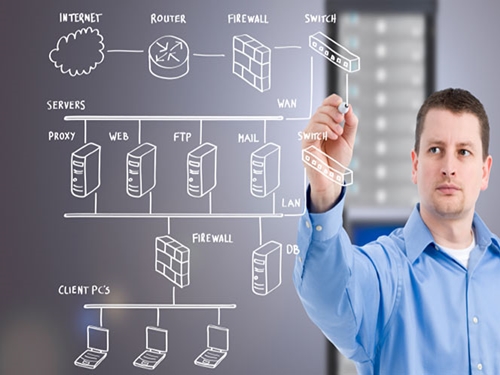
Yet, cyber security is not solely a concern for individuals—it's a collective responsibility that extends to organizations and governments alike. Enterprises must invest in cutting-edge security infrastructure and regularly update their defenses to stay ahead of emerging threats. This includes implementing firewalls, intrusion detection systems, and regular security audits to identify vulnerabilities before they can be exploited.
Moreover, collaboration and information sharing within the cyber security community are paramount. Threat intelligence platforms enable organizations to stay abreast of the latest cyber threats and adopt proactive measures to mitigate them. By pooling resources and expertise, we can collectively bolster our cyber defenses and stay one step ahead of cybercriminals.
Nevertheless, even the most robust cyber security measures can be circumvented by determined adversaries. As such, incident response planning is crucial for minimizing the impact of a successful breach. Rapid detection and containment are essential to prevent the spread of malware and limit the damage inflicted. Furthermore, post-incident analysis helps organizations learn from their mistakes and fortify their defenses against future attacks.
Looking ahead, the landscape of IT Support Melbourne will continue to evolve in tandem with technological advancements. The rise of artificial intelligence and machine learning offers promising avenues for enhancing threat detection and response capabilities. However, it also presents new challenges, as cybercriminals leverage these same technologies to orchestrate more sophisticated attacks.





Comments